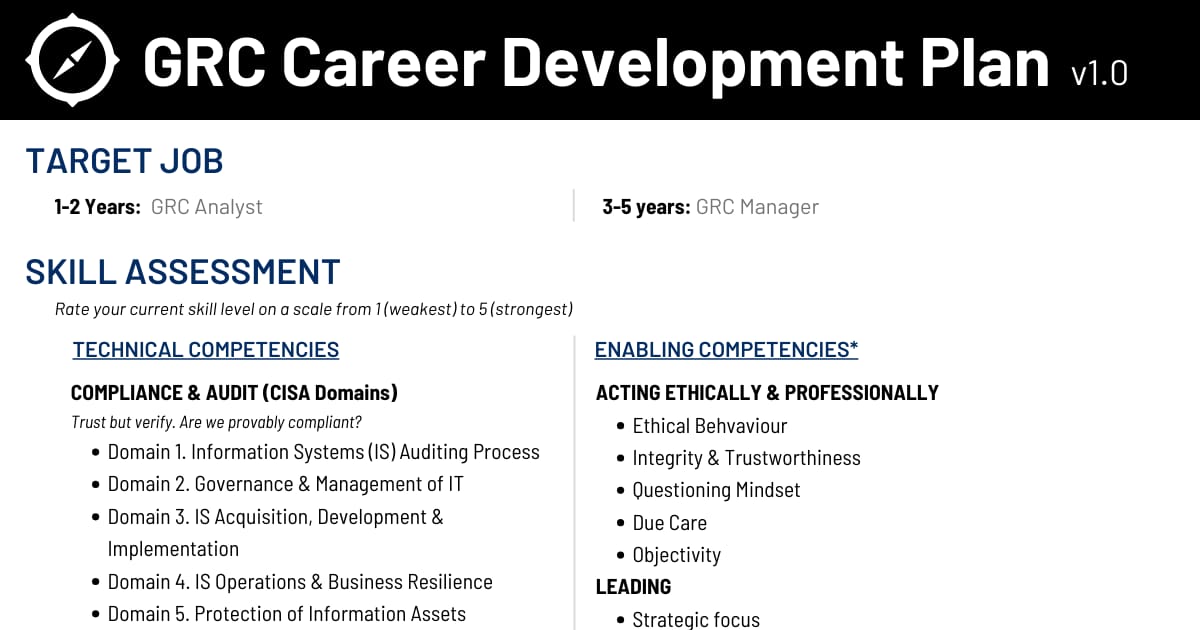
Table of Contents
Risk Management is Your Opportunity to Make an Outsized Impact
What you need more now more than ever, is a risk approach to managing your Security program, because you can't do everything at once. You have limited resources, limited budget, potentially unlimited attack surface that’s expanding all the time.
The Risk aspect of GRC can make a massive difference when you help prioritize the right programs and remediation work. If you can't do this, then you're going to spin your wheels on things that will be less effective than something closer to the root cause.
To reliably achieve objectives, organizations need cyber risk guard rails and due diligence in place. Not to slow you down but to help you avoid driving off a cliff. The fastest cars have the best brakes.
Start Here: Understanding a More Intense “What Could Go Wrong (WCGW)” Mindset
One of the first foundational concepts that was explained to me when I came to Cybesecuirty from Finance was a difference in mindset between COSO (Committee of Sponsoring Organizations of the Treadway Commission) in commercial industry compliance and the Rainbow Series of cyber controls that came from the Department of Defense.
It’s a bit more intense, so buckle up.
Grounded in this mindset, where to start?
Next, Anchor on the NIST SP800-30 Guide for Conducting Risk Assessments
From the alphabet soup of Risk literature you’ll see out there, this is my favourite guide that’s highly respected and happens to be free:
It’s a great read from cover to cover. To spark your curiosity and get you started, here are some core concepts I apply most commonly to my daily work:
Risk = function of Asset Value x Threats x Vulnerabilities
What Could Go Wrong in cybersecurity?
Critical data could be disclosed, altered, or denied access to
This can include a threat actor stealing your money that’s online, stealing or spoofing your identity to commit crimes or exfiltrate your secrets, typically for financial gain by a professional criminal organization, but it could also be from other actors and reasons listed in NIST 800-30
The bottom-line of what matters is “Residual Risk.” This is the risk left over after security controls have been applied. So focus more on that than Inherent Risk which is just an input to your assessment
Figure 3 below provides a nice 10,000 ft view of the process. from which you can jump to Appendices D through I for practical examples and guidance on
D. Threat sources,
E. Threat events,
F. Vulnerabilities,
G. Likelihood,
H. Impact
I. Risk determination

NIST SP800-30 Guide for Conducting Risk Assessments
Rolling various risk assessments up at the end of the month or quarter for an executive scorecard, apply the 5×5 residual risk matrix from Appendix I.
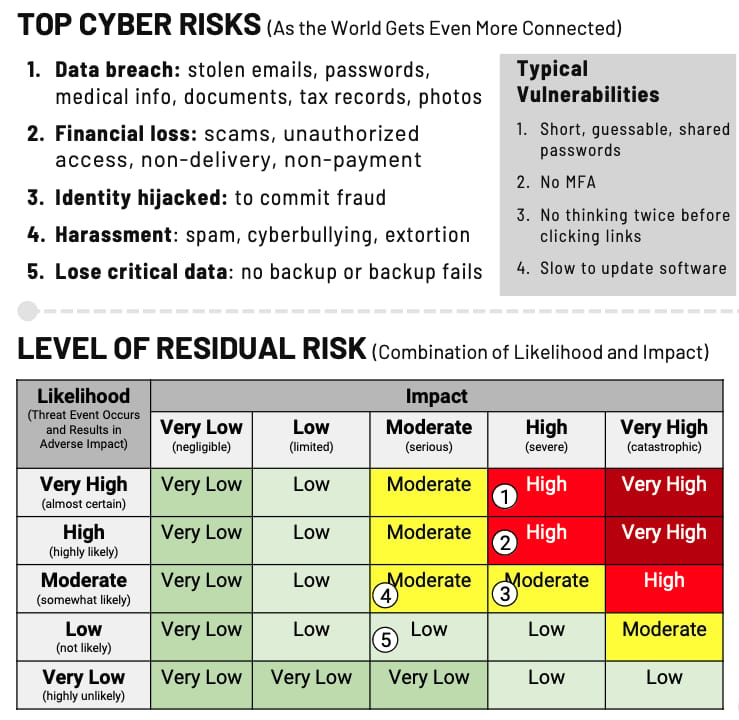
This example from my previous blog post/video on to make a Personal Cyber Safety Scorecard
Helpful Resource: create_threat_model
To advance your career development both by getting more technical and getting hands on experience with risks assessments, check out this awesome AI prompt by Daniel Miessler grounded in his Everyday Threat Modelling essay. It’s a great read from a seasoned 20 year practitioner and a powerful tool for risk assessments.
Another Helpful Resource: You Are a Target Poster
Another great resource to help make your comprehension of cybersecurity risk assessments more applied and specific to everyday life is this poster from SANS, based on the work by journalist Brian Krebs.
Most people don't think of themselves as a target for hackers or cybercriminals. We imagine we're too unimportant, or that our data and assets aren't valuable enough to attract interest. But the reality is, nearly everyone is a potential target in today's hyper-connected digital world. This important work is another reason that makes GRC careers compelling.
Question: What’s the Most Important Input to the Cybersecurity Risk Assessment Process?
Answer: An understanding of the information system.
Ideally you’ve operated or designed one. If you haven’t, load up technical competencies in your Career Development Plan.
Risk Assessment Template
Personal Cyber Safety Risk Assessment
OBJECTIVE
Cyber safety at home, for an individual, family that’s a beginner to this topic.
ASSET IDENTIFICATION
Asset | Examples |
|---|---|
Money | Bank and investment accounts, shopping accounts, PayPal, in-game currency, potentially cryptocurrency, NFTs |
Critical Data | Emails, photos, passwords, documents, tax filings |
Identity | Can be stolen for fraud (e.g. to apply for credit) or to commit crimes |
Privacy | In addition to controlling access to the digital assets listed above, there’s your digital exhaust of location, preferences, habits and more that can be monetized or weaponized if in the wrong hands |
THREAT EVENTS
Phishing
Deceptive emails or messages tricking users to reveal personal information, send money or click links with malicious payloads
Malware
Spyware, remote access trojan, adware, ransomware
Account reset/takeover
Credential stuffing
Password dumps/cracking
SIM swap attack
Wi-Fi Eavesdropping
Exposure of children to inappropriate content, cyber bullying, or criminals
Scams
Imposter
Identity theft
Non-Payment/Non-Delivery
Harassment or Extortion
THREAT SOURCES
Threat Actors
Professional Cybercriminals
Indiscriminately scanning Internet connected devices and accounts: “jiggling doorknob handles”
Opportunistic, non-professional
Hacktivists
Advanced
Motivations
Financial gain: directly or indirectly monetize your stolen data
Curiosity, boredom or thrill-seeking
Demonstration of skills
Coercion or manipulation
VULNERABILITIES
Weak passwords: easy to guess or the same password for multiple accounts
No Multi-factor authentication
Same email and/or phone number used for sensitive accounts (e.g. banking) and non-sensitive accounts (e.g. pizza order preferences)
Home modem/routers with default passwords and settings
Using public Wi-Fi
Lack of cybersecurity awareness
Poor cyber hygiene
Visiting unsafe websites
Mobile device and home PC vulnerabilities
RISK ANALYSIS
Top Risk | Likelihood | Impact | Residual Risk Level |
|---|---|---|---|
1. Data breach: e.g. emails, passwords, documents, tax records, photos stolen | Very High (Almost certain) | High | High |
2. Financial scams, or money/financial assets stolen | High (Highly likely) | High | High |
3. Identity hijacked to commit fraud | Moderate (Somewhat likely) | High | Moderate |
4. Harassment/spam/ cyberbullying/extortion | Moderate (Somewhat likely) | Moderate | Moderate |
5. Lose critical data: no backup or backup fails | Low (Not likely) | Moderate | Low |
90 DAY ACTION PLAN
What | When |
|---|---|
1. Inventory and stack rank online accounts by risk priority Email, Apple/Windows ID, Financial, Government, Shopping, Social Media, Chat, Photos, Online Services, Streaming, Vehicle, Utilities, Insurance, etc. | Month 1 |
2. Delete unused accounts and services | Month 1 |
3. Implement a Password Manager for unique, complex, 15+ character passwords | Month 2 |
4. Enable MFA | Month 3 |
5. Think before you click training | Month 3 |
6. Regularly update software training | Month 3 |
Bottom-Line
We can't eliminate risk entirely. New threats constantly emerge and our digital lives keep getting more complex. But by being proactive and strategic, we can dramatically reduce the likelihood and impact of an incident, which protect and enables the business.