Table of Contents
How to Get Workpapers Right
It doesn’t help much to be compliant if you’re not provably compliant. So GRC Analysts with portfolios of controls to assess spend a lot of time creating detailed records of their work performed, called “workpapers.”
It’s important to get workpapers right since they’re reviewed by your manager, Quality Assurance teams and potentially other groups looking to meet deadlines and have a solid basis for compliance attestations. They want you to include clear evidence of three things:
What you did
What you found
What you concluded
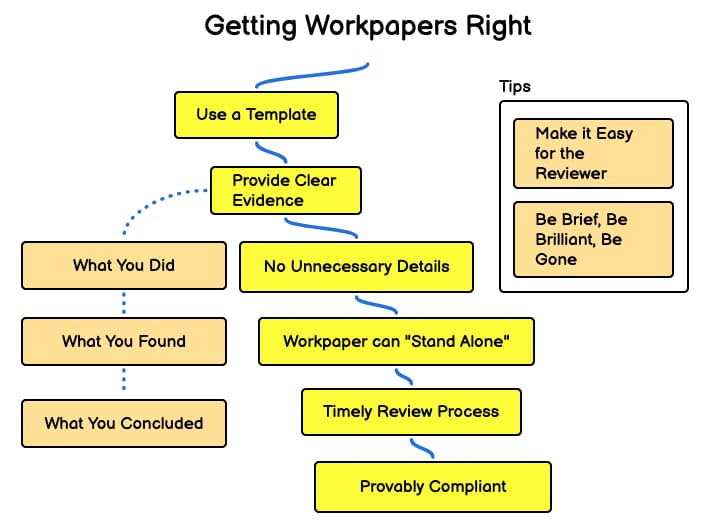
Since you’re writing for others here, it's important to be neat and consistent in how you present things. Templates help and are common, and I’ve included an example below.
The Best Audit Workpapers “Stand Alone,” But Only Include What’s Necessary
In practice I’ve seen this much more in accounting than cybersecurity, but ideally every workpaper should stand alone. That means comprehensive and self-sufficient, containing all the necessary information and evidence to support its conclusions without requiring additional context or you to be in the room explaining things to the reviewer.
But the most important thing is to include only what's necessary. Tell the reader what you did, what you found, and what you concluded. Resist the temptation to include other stuff that happens to be interesting or that caught your attention. Unnecessary workpaper content wastes your time and the reader's. Worse still, they may open up lines of inquiry that are irrelevant to the audit at hand.
Bottom-Line
If you make your workpapers complete, clear and include only what matters, you make it easy for others to understand the work you've done, which leads to great GRC outcomes. Get after it with the template below and let me know what you think!
Workpaper Template
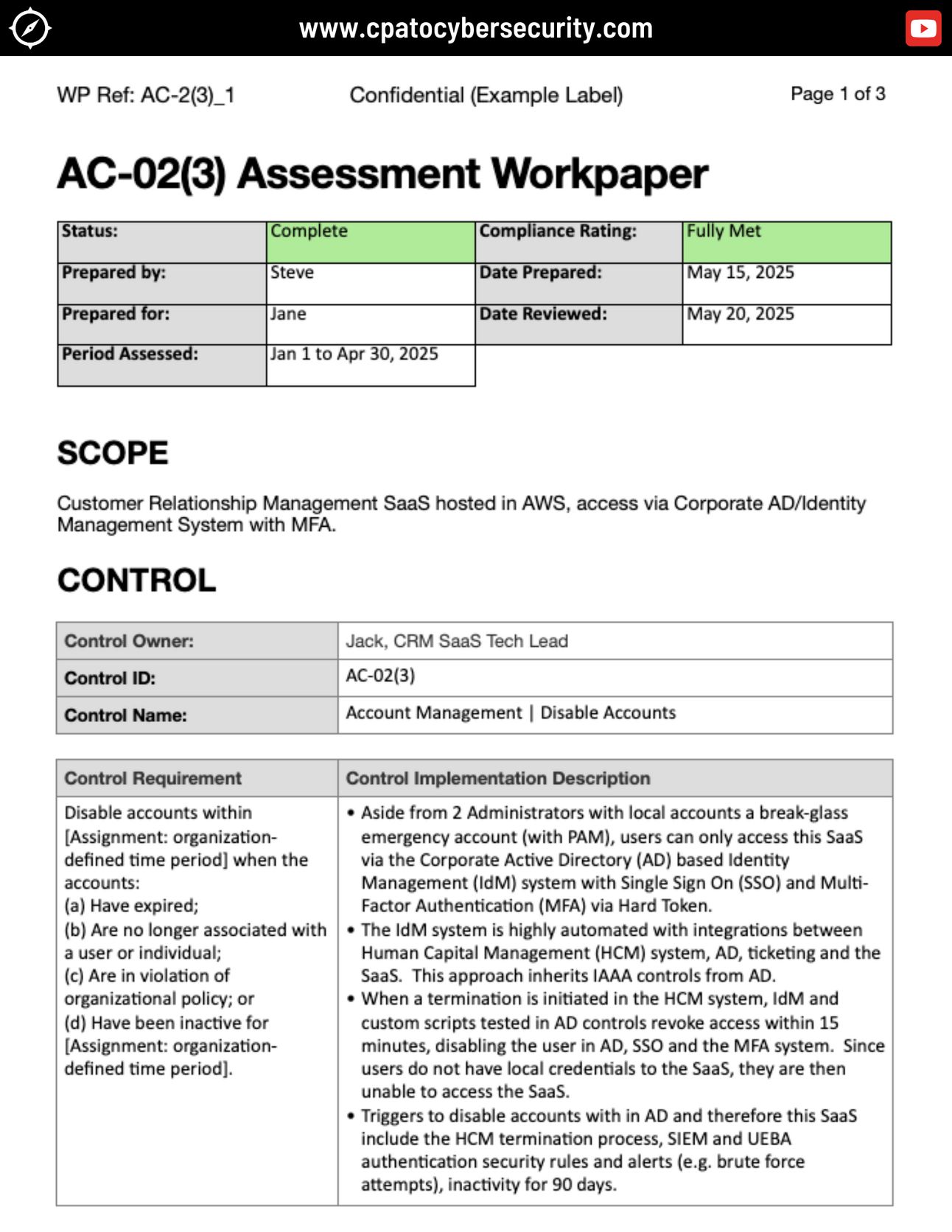
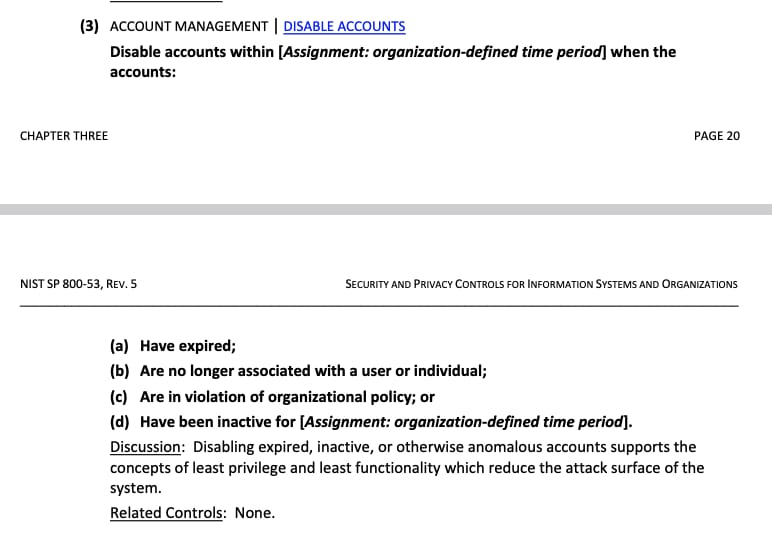
Note that the control requirement is from the “control dictionary” NIST SP800-53, for which this fictional company has written an Implementation Description for their environment.

Audit artifacts will be filed along with this workpaper, and are labelled as follows:
AC-02(3)_2 Access Control Policy
AC-02(3)_3 IdM and SaaS admin team procedures for disabling accounts
AC-02(3)_4 AD IAAA control testing workpapers
AC-02(3)_5 Human Capital Management (HCM) system headcount report
AC-02(3)_6 LDAP report of AD users
AC-02(3)_7 SaaS CRM user report
AC-02(3)_8 Screenshot of SIEM logs for AD authentication security events
AC-02(3)_8 CRM account inactivity report

Note that the test steps come from NISTSP 800-53A. It’s an excellent free resource.



