🔐 Simply Cyber Course Materials - Community Access Welcome! This content is shared with enrolled students as part of our commitment to inclusion and value delivery in cybersecurity education. We believe in supporting each other's learning journey through ethical collaboration. Please help us maintain this open educational environment by keeping this URL within our course community. Sharing this link publicly undermines our ability to freely provide these materials. Questions? Reach out to your instructor—we're here to support your success!
Table of Contents
📚️ Exam Objective 2.3
🔎 🌐 Review Network Configurations
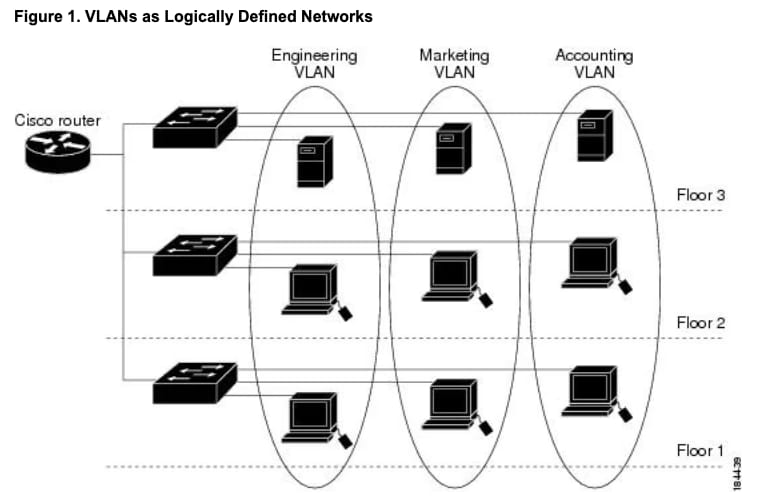
Subnetting/VLAN
Key Concepts:
Purpose: Compartmentalization to limit blast radius when a host is compromised
Traditional View: Departments segregated by function (e.g., Accounting subnet separate from HR)
Modern Reality:
Many organizations use cloud-based SaaS solutions (Financial SaaS, HRMS)
Risk-based segmentation often more practical than departmental segmentation
Collaboration needs make strict departmental segmentation challenging
Implementation Challenges:
Harder to implement than diagrams suggest in collaborative environments
Balance needed between security and business functionality
Consider using jump boxes as controlled checkpoints for network segment access
Can control both ingress and egress through specific network segments
Network Segmentation Benefits:
Limits blast radius during security incidents
Enables access control at segment boundaries
Allows selective network shutdown while maintaining other services
Protects critical systems from lateral movement
Common Network Types:
Flat Networks:
Single perimeter firewall (hard candy shell, soft interior)
Not ideal but may be acceptable for small businesses with budget constraints
Similar to "M&M" or "Cadbury egg" security model
Segmented Networks: Better security through compartmentalization
Micro-segmentation: Host-based firewalls on critical servers (e.g., IPtables on Linux)
Real-World Examples:
Medical device network segments (IOT/OT Lite environments)
May contain Windows XP, Windows 7, or even fully patched Windows 11
Vendor-maintained systems you can't patch directly
Vendors access via remote tools (TeamViewer, AnyDesk, LogMeIn)
Critical to isolate from EHR and business systems
Remove email capabilities from these vulnerable systems
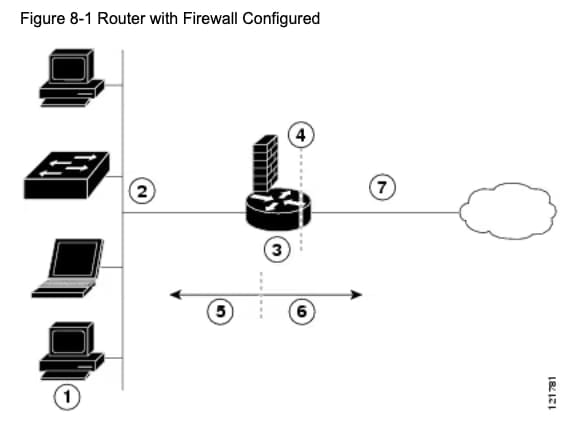
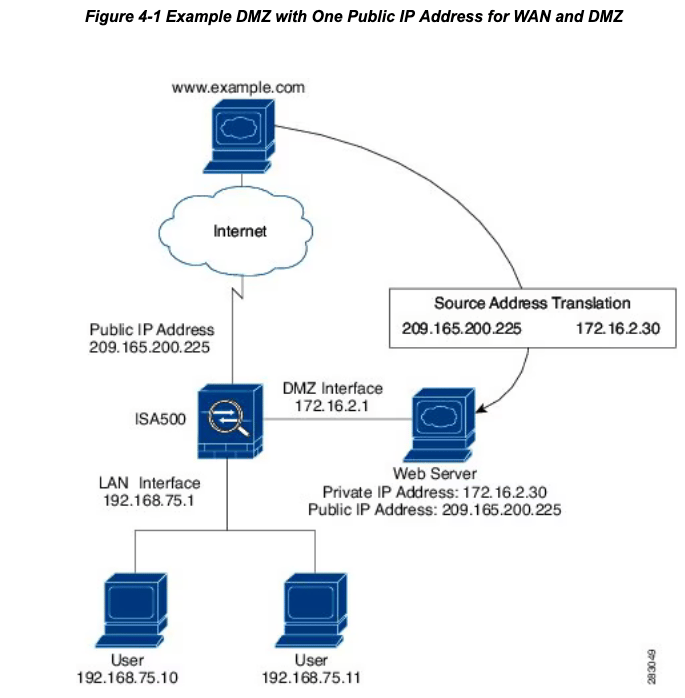
Firewall/DMZ
Key Implementation Considerations:
Firewalls act as compartmentalization mechanisms
Historical analogy: Like old building firewalls with rope-triggered doors
Modern analogy: Similar to submarine compartments that seal during breaches
Can enable selective network segment shutdown during incidents
GRC Professional Considerations:
MFA behind jump boxes may be redundant and damage credibility
Understanding when controls are appropriate shows competence
Need to balance security with operational requirements
Limited budgets require risk-based decision making
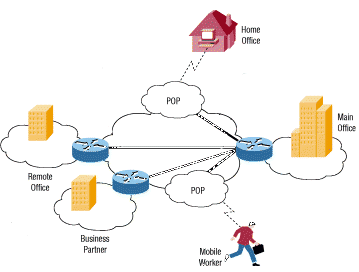
Virtual Private Networks (VPN)
Security Considerations:
Remote vendor access creates potential attack vectors
Similar risks to SolarWinds/Kaseya supply chain attacks
VPN connections can become reverse shells into your network
Need to control what's allowed into vulnerable network segments

🔎 🤖 Review Legacy System Configurations
Common Legacy System Challenges:
Windows XP, Windows 7, and other EOL operating systems still in production
Vendor-controlled systems that IT cannot patch or maintain
Medical devices and OT systems with long lifecycles
Contractual or legal restrictions on system modifications
Risk Mitigation Strategies:
Isolate legacy systems in dedicated network segments
Remove unnecessary capabilities (email, web browsing)
Implement compensating controls when patching isn't possible
Use host-based firewalls where network segmentation isn't feasible
Monitor vendor remote access sessions closely
GRC Professional Tips:
Don't recommend controls that don't make sense (e.g., MFA on jump box protected resources)
Understand the business and operational constraints
Focus on risk-based approaches rather than compliance checkboxes
Consider budget limitations when recommending solutions
Build credibility by understanding technical implementation details
Key Takeaways
Budget Reality: Not every organization can afford ideal network segmentation
Risk-Based Approach: Make decisions based on actual risk, not textbook ideals
Political Capital: Avoid losing credibility by recommending impractical controls
Business Context: Segmentation should support business operations, not hinder them
Compensating Controls: When ideal solutions aren't possible, implement alternatives
Collaboration: Work with network engineers and understand their perspective
Field Work: Real-world scenarios often differ from textbook examples