I just completed Tyler Ramsbey's Intro to AWS pentesting course, approaching it from a GRC professional's perspective. The results were sobering: An environment passing 82% of Cloud Security Posture Management checks was completely compromised in under 30 minutes.
Switching to this side of the keyboard in simulated attack scenarios helps GRC practitioners to:
Ask better risk assessment questions
Speak the same language as more technical teams
Prioritize remediation based on actual exploit paths
If you'd like to join me in sharpening your technical acumen to narrow the gap between GRC and offensive security, try the "AWS Beanstalk Secrets" scenario here, check out my walkthrough below, and of course consider Tyler's awesome course. As he would say, "Happy Hacking!"
Table of Contents
Prerequisites
AWS Account
Create a free account
Set up a $0.1 budget alert
Also remember to destroy your CloudGoat scenarios after completing the walkthrough to avoid unexpected AWS charges. Run
cloudgoat destroy beanstalk_secretswhen finished.
VirtualBox with Kali
Install VirtualBox
Install Kali
Install the AWS CLI for Kali
Install Terraform on Kali
Notion
I prefer Obsidian as a daily driver for notes but its SaaS offering has a cost, so a free Notion account comes in handy for pen test challenges like this, synching in real time between your laptop and Kali on your Virtual Machine
Flameshot
apt install flameshotI learned about this app in the course and it works well
Pacu AWS Exploitation Framework
pipx install git+https://github.com/RhinoSecurityLabs/pacu.gitCloudGoat
pipx install cloudgoatCreate the “beanstalk_secrets” Scenario
beanstalk_secrets (Easy)
cloudgoat create beanstalk_secrets
In this scenario, you are provided with low-privileged AWS credentials that grant limited access to Elastic Beanstalk. Your task is to enumerate the Elastic Beanstalk environment and discover misconfigured environment variables containing secondary credentials. Using these secondary credentials, you can enumerate IAM permissions to eventually create an access key for an administrator user. With these admin privileges, you retrieve the final flag stored in AWS Secrets Manager.
Contributed by Tyler Ramsbey
Attack Scenario Overview
⚠️ IMPORTANT SECURITY DISCLAIMER: The techniques demonstrated in this walkthrough are for educational purposes only and should ONLY be performed in authorized environments such as your own AWS account with CloudGoat scenarios. Unauthorized access to computer systems is illegal and unethical. Always ensure you have explicit permission before testing any security measures. Misuse of these techniques could result in criminal charges, termination of employment, and civil liability.
The Vulnerable Environment
What is Elastic Beanstalk?
AWS Elastic Beanstalk is a Platform-as-a-Service (PaaS) that simplifies deploying and scaling web applications. Despite its widespread use, Elastic Beanstalk is frequently overlooked in security assessments. Security teams often focus on EC2 instances and Lambda functions while missing Beanstalk environments entirely. This oversight is critical because developers frequently store API keys, database credentials, and other sensitive data in Beanstalk environment variables, treating them as a secure configuration store when they're actually accessible to anyone with basic read permissions.
Example Use Case
Attack Chain Summary
Enabling AWS Services Before the Attack
To help our understanding of the vulnerabilities in this cloud environment before, during and after the attack, let’s enable some helpful native AWS services.
AWS Security Hub CSPM
Security Hub CSPM (Cloud Security Posture Management) provides centralized security findings and compliance monitoring.
.
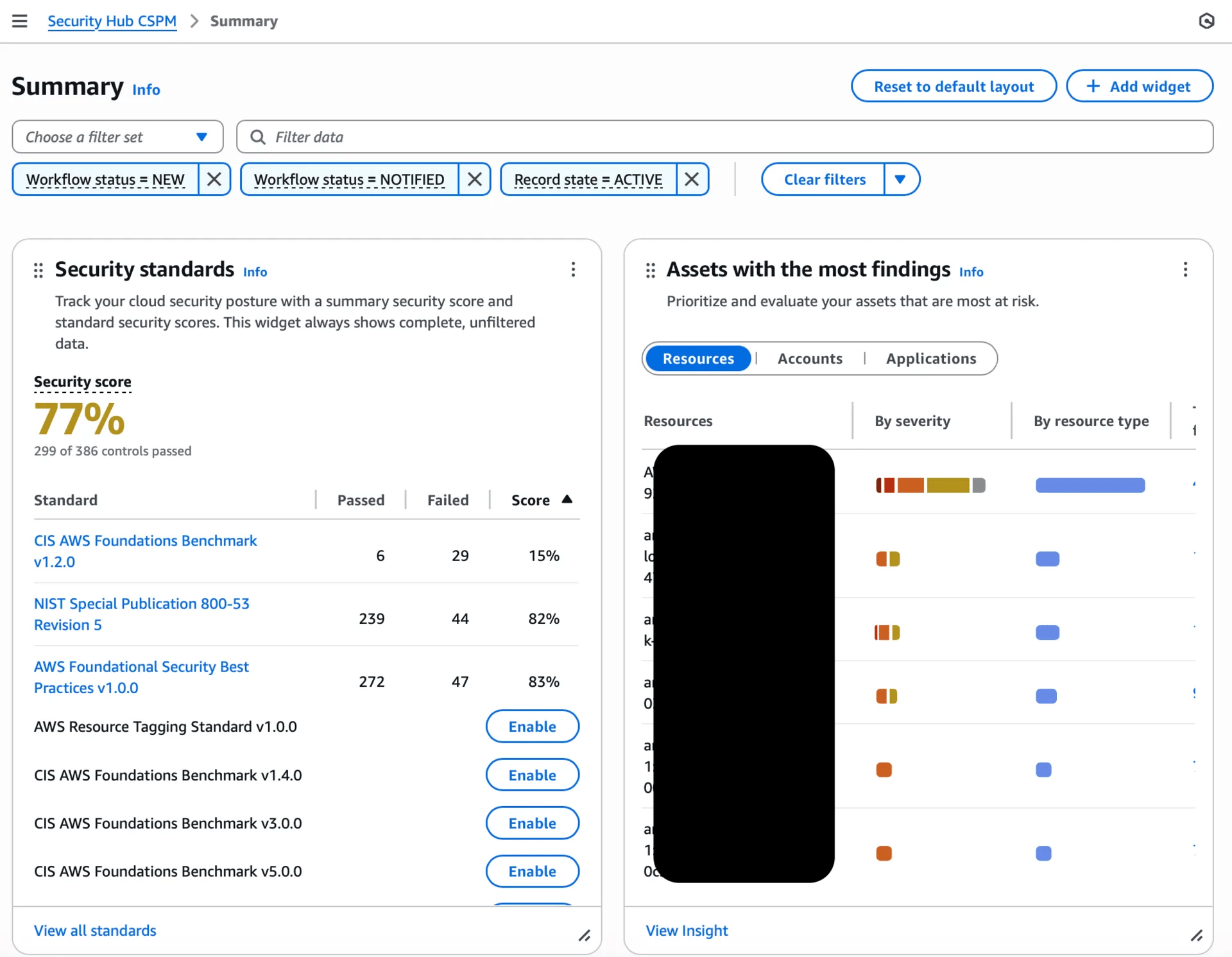
It takes about 15 minutes to complete the first scan, which runs daily. Before the attack even begins we see a security score of only 77% and 120 findings raised in this intentionally vulnerable (for practicing pen test techniques) environment.
GuardDuty Threat Detection
GuardDuty uses machine learning to identify malicious activity and unauthorized behavior.






