Table of Contents
Preface
Unsafe At Any Speed: CISA's Plan to Foster Tech Ecosystem Security | Black Hat
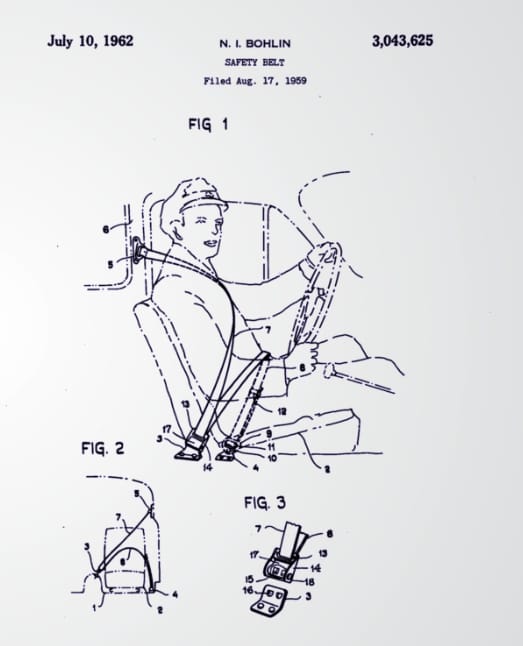
In 1965, Ralph Nader published "Unsafe at Any Speed", a survey of automobile safety from design, to delivery, to maintenance. The parallels to the safety of modern technology are startling.
Exam Objectives 📚
Candidates must be able to understand the key concepts related to the NIST Cybersecurity Framework. Students will be able to:
1.3 Summarize how the NIST Cybersecurity Framework is different than other frameworks and certifications:
Other frameworks and informative references:
International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) 27001 and 27002
National Institute of Standards and Technology (NIST) Special Publications
SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach
SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
SP 800-171 Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
SP 800-218 Secure Software Development Framework (SSDF)
SP 800-221A Integrating ICT (Information and Communications Technology) Risk Management Programs with the Enterprise Risk Portfolio
Cyber Risk institute (CRI) Profile
Center for Internet Security (CIS) Critical Security Controls
ITIL
Payment Card Industry Data Security Standard (PCI DSS)
Health Insurance Portability and Accountability Act (HIPAA)
North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection(CIP) Standards
Federal Risk and Authorization Management Program (FedRAMP)
Open Web Application Security Project (OWASP)
Cloud Security Alliance (CSA) Security, Trust, and Assurance Registry (STAR)
2.4 Summarize how the NIST Cybersecurity Framework outcomes are related to controls provided by other publications

Controls 🔒
Term | Definition | So What? |
|---|---|---|
Controls | Specific measures, practices, or safeguards that organizations implement to manage and mitigate cybersecurity risks | Tangible actions or mechanisms that help prevent, detect, respond to, and recover from cybersecurity incidents Chapter 3 Review: Technical, Operational, Managerial (Administrative) |
In most frameworks, controls are a requirement that must be followed.
Voluntary Nature of the NIST Cybersecurity Framework 🙋
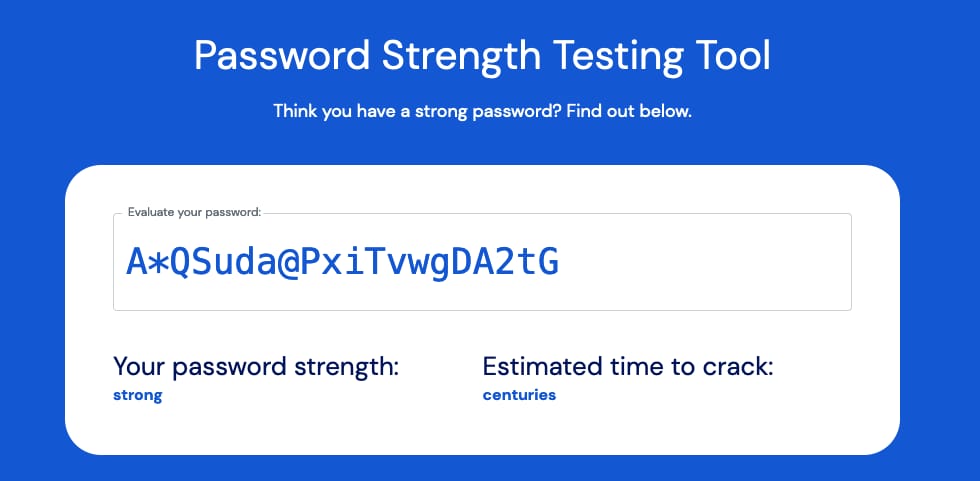
Password Complexity Requirements
Is this secure?
A*QSuda@PxiTvwgDA2tG
Other Options to Improve Authentication Security
Multi-Factor Authentication (MFA): This method requires users to provide two or more verification factors to gain access to a resource such as an application, online account, or a VPN. Common factors include something you know (password or PIN), something you have (a smartphone or hardware token), and something you are (biometrics: fingerprint scans, facial recognition, or iris scans).
Using Known Password Lists: Implementing checks against lists of known compromised passwords can prevent users from choosing passwords that are already exposed and easy to guess. This can be particularly effective in stopping common and repeated password-related vulnerabilities.
Time-based One-time Password (TOTP): This is an algorithm that generates a one-time password which is valid only for a short period of time, providing an additional layer of security by ensuring that the password is not reusable.
Geographic and IP Restrictions: Limiting access based on geographic location or IP addresses can help prevent unauthorized access from high-risk areas or unfamiliar sources.
Anomaly Detection and Login Monitoring: Tools that monitor login attempts and detect anomalies (like logins from new devices or locations) can trigger additional authentication requirements or alerts.
Profiles
With CSF, the organization has the power to choose the proper controls from any source needed to deliver the outcomes chosen in the target profile
Outcomes 📈
Term | Definition | So What? |
|---|---|---|
Outcomes | The desired result or objective that an organization aims to achieve through implementing cybersecurity controls and practices, focusing on those measures' overall effectiveness and impact | A change or result the organization expects to observe from a given process or action CSF has outcomes specific to each category and subcategory They provide guidance on the intended goals and results that an organization should strive for |
Do Outcomes = Requirements?
PR.DS-11 Outcomes
“Backups of data are created, protected, maintained, and tested.”
PR.DS-11 Testable Questions for Internal Assessment
How are backups of data created?
How are backups of data protected?
How are backups of data maintained?
How are backups of data tested?
DE.CM-02 Outcomes
The physical environment is monitored to find potential adverse events
DE.CM-02 Testable Questions for Internal Assessment
Are security cameras along the perimeter to monitor our physical environment?
Are security guards hired to roam throughout the building to actively monitor their facilities?
24×7?
Should we install an eight-foot tall, barbed wire fence with motion sensors?
When was the last physical penetration test to determine if the physical environment is being properly secured?
Up to the Organization What Best Meets Their Needs
Data center that contains credit card processing systems?
PCI-DSS contractual obligations may require a physical pen test, with a Payment Card Industry certified external consultant
Health care provider?
Health Insurance Portability and Accountability Act (HIPAA) requirements, might benefit from that same pen test
CSF maps to them both
Helpful overarching framework for “test once, assure many”
Flexibililty
CSF only requires that you achieve your desired outcome.
For DE.CM-02 this could be:
Identify and remediate 98% of known physical intrusion vulnerabilities within 90 days of discovery
Or 90% in 120 days
To verify compliance, you could have
External consultant pen tests every 90 days
Or internal pen tests every year
Scalability

Informative References 📖
Term | Definition | So What? |
|---|---|---|
Informative References | An informative reference is a specific section of standards, guidelines, and practices that illustrates a method to achieve the outcomes associated with each category and subcategory. | If your organization wants to combine CSF with more prescriptive control-based frameworks in its compliance portfolio, it certainly can! |
CSF: PR.DS-01 The confidentiality, integrity and availability of data-at-rest are protected
CIS 3.11 Encrypt Sensitive Data at Rest
SP 800-53 SC-28: Protection of Information At Rest
ISO/IEC 27001 and 27002
The International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) 27001 and 27002 framework is a set of international standards that provide guidelines and best practices for establishing, implementing, maintaining, and continually improving an information security management system (ISMS).
ISO/IEC 27001 specifies the requirements for establishing and maintaining an ISMS
ISO/IEC 27002 provides a comprehensive set of controls and implementation guidance for information security management
NIST Special Publications
National Institute of Standards and Technology (NIST)
SP 800-37 Risk Management Framework for Information Systems and Organizations
SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
SP 800-171 “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations”
SP 800-218 "Secure Software Development Framework (SSDF)
SP 800-221A Information and Communications Technology (ICT) Risk Outcomes
CRI
Cyber Risk Institute, a not-for-profit coalition of financial institutions and trade associations whose aim is to protect the global economy through cyber resiliency and standardization
CIS CSC
The Center for Internet Security (CIS) Critical Security Controls (CSC)
Three Implementation Groups:
Basic
Foundational
Organizational
Solid Foundation of Controls
Practical
Adaptable
COBIT 5
Control Objectives for Information and Related Technology (COBIT 5)
Developed by the Information Systems Audit and Control Association (ISACA)
Systematic
Clear Governance and Management
Structured Approach
ITIL
Information Technology Infrastructure Library,
Best practices for information technology service management (ITSM)
34 individual practices
PCI DSS
Payment Card Industry Data Security Standard (PCI DSS)
Secure environment for cardholder data
Specific control objectives and requirements
HIPPA
Health Insurance Portability and Accountability Act (HIPAA)
The Privacy Rule
The Security Rule
NERC CIP
North American Electric Reliability Corporation (NERC)
Critical Infrastructure Protection (CIP)
Consistent and effective cybersecurity posture across the electric power industry
FedRAMP
Federal Risk and Authorization Management Program (FedRAMP)
Streamline the process of assessing and authorizing cloud services
STAR
Cloud Security Alliance (CSA)
Security, Trust, and Assurance Registry (STAR)
Cloud service providers
Transparency and accountability in delivering secure services
Ensure a higher level of confidence in the security and trustworthiness
OWASP
Open Web Application Security Project (OWASP)
Conclusion and Touchpoints ✅
For the AKYLADE certification exams:
Have a basic understanding of the types of information these frameworks contain
They can be used as sources for controls to achieve the organization’s desired outcomes within the NIST Cybersecurity Framework.
CSF is
Generic and broad
Non-prescriptive
Allows flexibility