Table of Contents
Exam Objectives 📚
Understanding risk management is crucial before diving into the NIST Cybersecurity Framework. This chapter aims to provide a solid foundation in risk management, equipping you with the knowledge and terminology needed to navigate the complex landscape of cybersecurity.
By grasping these fundamentals, you'll be better prepared to identify, assess, and mitigate risks, ensuring the security and resilience of digital systems and assets.
Candidates must be able to understand the key concepts related to risk management. Students will be able to:
5.1 Explain the fundamentals of risk management
Risk Analysis
Qualitative
Likelihood of Risk
Impact of Risk
Quantitative
Single-Loss Expectancy (SLE)
Annualized Rate of Occurrence (ARO)
Hybrid
Risk Appetite
Risk Tolerance
Business Impact Analysis
Recovery Time Objective (RTO)
Recovery Point Objective (RPO)
Mean Time to Repair (MTTR)
Mean Time Between Failures (MTBF)
Single Point of Failure
Mission Essential Functions
Identifying Critical Systems
Financial Analysis
Total cost of Ownership (TCO)
Return on Investment (ROI)
Return on Assets (ROA)
5.2 Given a scenario, determine the appropriate risk response and to a given threat or vulnerability
Risk Responses
Acceptance
Avoidance
Transference
Mitigation
Types of Risk
Inherent Risk
Residual Risk
Risk Register
5.3 Given a scenario, assess cybersecurity risk and recommend risk mitigations
Identify threats to an organization
Identify vulnerabilities to an organization
Identify risks to an organization
Recommend specific risk mitigations
Determine benefits of a particular risk mitigation
Determine the trade-offs of a particular risk mitigation
Evaluate the effectiveness of a particular risk mitigation
Develop a risk management plan
Develop a cybersecurity strategy
Risk Management Fundamentals 🧱
Term | Definition | So What? |
|---|---|---|
Risk | The potential for loss, damage, or harm resulting from the occurrence of threats exploiting vulnerabilities in digital systems or assets | Cyber risk has catapulted higher in board room priorities, to become an existential business risk |
Risk Management | The systematic process of identifying, assessing, prioritizing, and mitigating potential risks to an organization’s digital systems, networks, data, and assets to ensure their confidentiality, integrity, and availability | Guard rails and due diligence to reliably achieve objectives Not to slow you down. Consider that the fastest cars have the best brakes |
Risk Management Lifecycle | A systematic and iterative approach to managing risks by encompassing several phases | It’s a process, like Accounting |
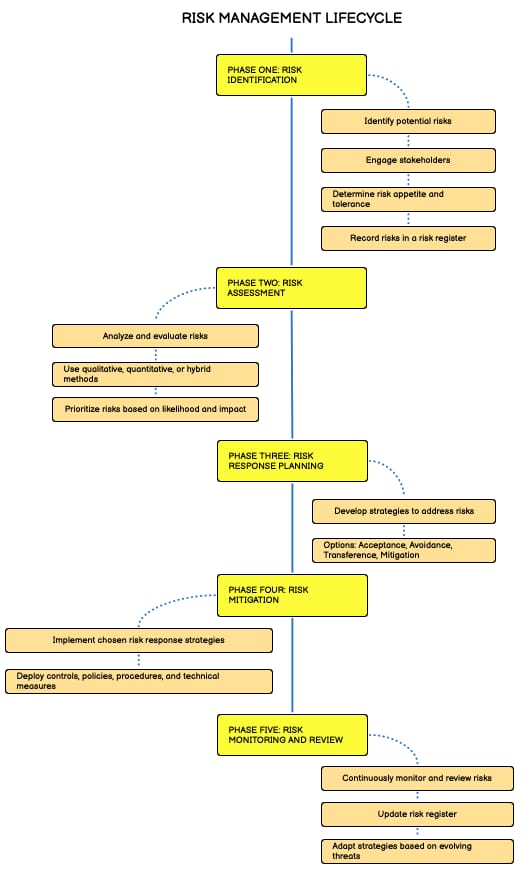
Risk Management Lifecycle 🔄
Risk management is a systematic process that involves identifying, assessing, prioritizing, and mitigating potential risks to an organization’s digital systems, networks, data, and assets. This process is essential for achieving cyber resilience. The risk management lifecycle provides a structured approach to managing risks through several phases:
Phase One: Risk Identification 🔍
This phase involves identifying potential risks through various methods:
Risk assessments
Threat intelligence
Stakeholder input
Term | Definition | So What? |
|---|---|---|
Stakeholders | An individual or group with an interest or influence in the organization’s digital systems and assets, whose perspectives and requirements may shape risk management strategies and decisions | Get ready to adapt your communication style as a translator between business (CEO, CFO) and technical (CIO, CTO) stakeholders Also between executive 30k ft views and front line operators (system administrators, end users) There are both internal and external stakeholders |

Term | Definition | So What? |
|---|---|---|
Supplier | An external entity that provides goods, services, or resources to an organization | If a supplier with your company’s critical data and has a breach, it will be your company name in the headlines, not theirs Also consider the shared responsibility model |
Target Data Breach: hackers gained access to Target's network through credentials stolen from a heating, ventilation, and air conditioning (HVAC) subcontractor named Fazio Mechanical Services
Term | Definition | So What? |
|---|---|---|
Risk Appetite | The organization’s willingness and tolerance level for accepting potential risks | As Cyber Risk Managers, we are a compass to help management make decisions |
Risk Tolerance | The level of risk that an organization is willing to accept in pursuit of its objectives before action is deemed necessary to reduce it | Both excessive security friction and insufficient security can sink the boat Success in business hinges on effective prioritization |

Security Organization Size and Budget Considerations
The risk appetite guides decision making processes to align risk management strategies with business objectives and priorities.
Financial institution 🏢: may have a Low Risk Appetite
Prioritize extensive security controls and stringent compliance measures to minimize the likelihood of data breaches.
Invest heavily in robust encryption mechanisms, implement strict access controls, and regularly conduct vulnerability assessments to ensure a high level of protection.
Technology-based startup 💻: may have a High Risk Appetite and be more willing to accept innovation and rapid growth risks.
Adopt agile development methodologies
Embrace emerging technologies
Allocate resources to explore cutting edge technologies while acknowledging that some vulnerabilities or risks may arise as a result of this more dynamic approach
This is why understanding the organization’s risk appetite is important.
Your recommendations to help manage risk need to be in alignment with the organization’s risk appetite so that you can align the appropriate risk management strategies to that organization to ensure a balance between increasing system security, growing business, and their overall strategic objectives.
Phase Two: Risk Assessment ⚖

Once risks are identified, the next step is to assess them. This involves analyzing and evaluating risks to determine their likelihood of occurrence and potential impact. There are different approaches to conducting risk analysis: qualitative, quantitative, and hybrid methods.
Term | Definition | So What? |
|---|---|---|
Quantitative Risk Analysis | Involves evaluating risks using numerical values and metrics to assess the financial impact and frequency of risk events | More objective and measurable E.g. Single Loss Expectancy (SLE), the Annualized Loss Expectancy (ALE), and Annualized Rate of Occurrence (ARO) Ranch analogy: Don’t buy a fence more expensive than the horse you’re protecting! |
Qualitative Risk Analysis | Risks are assessed based on subjective judgments, such as the likelihood and impact of a risk using a scale (e.g. low, medium, high) instead of a numerical metrics or figures | Numerical metrics are ideal but often hard to quantify and/or get reliable data for. E.g. for % completion of security patches: how would you measure that in diverse IT environments with multiple operating systems, applications, hardware/cloud? What timeframe is reasonable and how is it tracked from patch release to full deployment? Do you count pushing the patches or confirming they were received? |
Hybrid | Combines qualitative and quantitative approaches to assess risks by incorporating subjective judgments and numerical metrics to understand the likelihood, impact, and financial implications of the identified risks | Provides a more comprehensive understanding of risks by leveraging the strengths of both methods |
Straight Math: Quantitative Risk Analysis
Term borrowed from:

Understand, Manage, and Measure Cyber Risk: Practical Solutions for Creating a Sustainable Cyber Program
Term | Definition |
|---|---|
Single Loss Expectancy (SLE) | The metric used to estimate the potential Financial loss of an organization may experience from a single risk event occurrence |
Asset Value (AV) | The financial worth of the asset at risk |
Exposure Factor (EF) | The percentage of loss that would occur if the asset were compromised |
SLE = AV x EF | Single Loss Expectancy (SLE) = Asset Value (AV) x Exposure Factor (EF) |
ALE = SLE x ARO | Annualized Loss Expectancy (ALE) = Single Loss Expectancy (SLE) x Annualized Rate of Occurrence (ARO) |
Annualized Loss Expectancy (ALE) | The metric used to estimate the expected Financial loss over specified time resulting from particular risk |
Annualized Rate of Occurrence (ARO) | The estimated frequency at which specific risk event is expected to occur within a year |
Exercises
Question 1:
How do you calculate the Single Loss Expectancy (SLE) for an organization's web server with an Asset Value of $100,000 and an Exposure Factor of 60%, and what does the SLE represent?
Answer 1:
SLE=Asset Value×Exposure Factor
SLE=$100,000×0.60
SLE=$60,000
The SLE represents the potential financial loss the organization could face if the risk materializes. In this example, the organization could potentially face a financial loss of $60,000. Understanding the SLE allows organizations to prioritize their risk mitigation efforts based on the potential financial impact of different risks.
Question 2:
How do you calculate the Annualized Rate of Occurrence (ARO) for a risk event expected to occur three times every 10 years?
Answer 2:
ARO=3/10
This means the risk event is expected to occur 0.3 times per year.
Question 3:
How do you calculate the Annualized Loss Expectancy (ALE) if the Single Loss Expectancy (SLE) is $50,000 and the Annualized Rate of Occurrence (ARO) is 0.2, and what does the ALE represent?
Answer 3:
ALE=SLE×ARO
ALE=$50,000×0.2
ALE = $10,000
The ALE represents the average annual financial loss the organization can expect to face due to that specific risk. In this example, the organization can expect to face a financial loss of $10,000 per year.
Not So Straight Math: Qualitative Risk Analysis
In Qualitative Risk Analysis, risks are assessed based on subjective judgments, such as the likelihood and impact of a risk using a skill instead of a numerical metrics or figures.
The term likelihood refers the probability of a risk event occurring
Impact refers to the magnitude of its consequences.
By assigning qualitative values using a scale such as low, medium, or high for each of these factors, an organization can gain a broad understanding of the risks significance and prioritize them accordingly within the risk register.
For example, a high likelihood and impact risk would require immediate action and mitigation or measures, while a low likelihood and low impact risk may be considered a lower priority.
These resulting prioritizations can also help the organization determine which risks should receive more or fewer resources to be mitigated or resolved.
Hybrid Risk Analysis
Combines qualitative and quantitative approaches to assess risks by incorporating subjective judgments and numerical metrics to understand the likelihood, impact, and financial implications of the identified risks
This combined approach can provide a more comprehensive understanding of risks by leveraging the strengths of both methods.
This allows organizations to consider factors beyond financial impact, such as reputation, regulatory compliance, operational disruptions, and monetary assessments.
By combining these approaches, organizations can gain a nuanced perspective of the risks potential consequences and make informed decisions about risking mitigation strategies.
Phase Three: Risk Response Planning 📋
After assessing risks, the next phase is risk response planning. This involves developing strategies and action plans to address identified risks. The main strategies include risk acceptance, risk avoidance, risk transference, and risk mitigation.
Risk Acceptance
Acknowledging the existence of a risk without taking further action to avoid, transfer or mitigate it
To consider when the cost of implementing risk mitigation measures outweighs the potential impact of the risk.
E.g. a small business may accept the risk of a minor data breach due to limited resources and instead focus on investing their limited resources in their Core Business operations.
Monitor the risk and be prepared to respond if the impact exceeds the acceptable threshold based on the organization's risk appetite
Risk Avoidance
Eliminating or minimizing risks by avoiding activities that pose significant threats.
Modify business processes, technologies, or operational practices.
Example 1: avoid the risk of a third-party data breach by maintaining strict in-house data storage and processing capabilities instead of relying on external service providers.
Example 2: decommissioning a legacy system that is no longer supported by the vendor
Risk Transference
Shifting the potential impact of a risk to a third party through contracts or insurance.
Example 1: cyber insurance
Example 2: Instead of allowing credit card data in your IT environment, process payments through a PCI DSS compliant vendor who only sends you anonymized tokens
Risk Mitigation
Reducing the impact or likelihood of a risk event by implementing controls and safeguards.
Mitigation measures can include technical solutions, process improvements, employee training, and policy enforcement.
For instance, an organization might mitigate the risk of unauthorized access to its Network by implementing multi-factor authentication, encryption, and regular security patch updates on its systems.
Risk mitigation aims to minimize the potential consequences of risk and enhance the organization's resilience to the cyber threats.
Phase Four: Risk Mitigation 🛡

In this phase, organizations implement their chosen risk response strategies. This involves deploying appropriate controls, policies, procedures, and technical measures to reduce vulnerabilities and minimize the impact of potential threats. Technical controls like firewalls and encryption play a vital role in this phase.
Controls and Safeguards
During the risk mitigation phase, organizations will identify specific measures and actions to address the identified risks effectively.
This involves a systematic and comprehensive approach to implementing controls and safeguards tailored to the unique characteristics of each risk.
These measures are designed to strengthen the organization’s security infrastructure, enhance incident response capabilities, and protect critical assets and systems from potential threats.
Technical Controls
Technical controls involve the use of technology to protect systems and data.
User Authentication and Authorization: Ensuring only authorized individuals can access systems and data.
Encryption: Protecting data by converting it into a secure format that cannot be easily accessed by unauthorized users.
Patch Management: Applying updates to software to correct vulnerabilities.
Data Backup: Regular backups of critical data to ensure it can be restored in case of loss or corruption.
Endpoint Protection Platform (EPP): Prevent malware and other threats by securing endpoint devices through antivirus, anti-malware, and other protection features.
Endpoint Detection and Response (EDR): Monitor and collect data from endpoint devices to detect, investigate, and respond to threats and incidents.
Network Firewalls: Devices that prevent unauthorized access to or from a private network.
Intrusion Detection Systems (IDS): Tools that monitor network or system activities for malicious actions or policy violations.
Intrusion Prevention Systems (IPS): Automatically take action to block or mitigate malicious network traffic activities.
Security Information and Event Management (SIEM): Systems that provide real-time analysis of security alerts generated by hardware and software.
Operational Controls
Asset Management: Inventory and management of hardware and software assets to ensure they are securely maintained.
Change Management: Procedures for managing changes to IT systems to ensure they do not introduce new vulnerabilities.
Business Continuity Planning (BCP): Strategies for maintaining operations during and after a disruptive event.
Disaster Recovery Planning (DRP): Plans for restoring IT systems and data following a disaster.
Monitoring and Auditing: Continuous monitoring of systems and regular audits to detect and respond to security incidents.
Incident Response Procedures: Steps to address and resolve security incidents, minimizing damage and recovery time.
Managerial (Administrative) Controls
Managerial controls involve policies, procedures, and practices that help manage the cybersecurity program within an organization.
Policies and Procedures: Establish guidelines and rules for cybersecurity practices (e.g., acceptable use policy, data protection policy).
Risk Management: Processes for identifying, assessing, and mitigating risks.
Security Training and Awareness: Programs to educate employees about cybersecurity risks and safe practices.
Vendor Management: Policies for assessing and managing the cybersecurity posture of third-party vendors.
Penalties for non-compliance: Implemented and enforced
Phase Five: Risk Monitoring and Review 📉
The final phase involves continuously monitoring the effectiveness of risk mitigation measures and identifying new risks. Regular reviews and updates ensure that risk management strategies remain aligned with the organization’s objectives and evolving threat landscape.
This phase involves continuously monitoring the effectiveness of risk mitigation measures, identifying new risks, and reassessing existing risks as the business and threat landscape evolves.
Regular reviews and updates to the risk register ensure that risk management strategies remain aligned with the organization's objectives and risk appetite.
An organization's continual monitoring an assessment can ensure the effectiveness of its implemented controls.
The organization should conduct regular vulnerability scans, penetration testing, and security audits to identify emerging risks or potential weaknesses.
By proactively identifying and addressing vulnerabilities and evolving threats, organizations can adapt their risk mitigation strategies and prevent potential risks from being exploited.
Inherent Risk and Residual Risk ⚠
Understanding inherent and residual risks is essential for effective risk management. Inherent risk refers to the level of risk in an organization’s systems without any control measures. Residual risk is the level of risk that remains after implementing mitigation measures.
Term | Definition | So What? |
|---|---|---|
Inherent Risk | The level of risk in an organization's systems or processes without any control measures or risk mitigation efforts | Baseline risk to inform control selection and performance |
Residual Risk | The level of risk that remains after implementing risk mitigation measures | The “bottom line,” current state risk level |
Why do we need both? 🤔
By assessing inherent risk, organizations understand the Baseline risk landscape.
They can identify areas where significant vulnerabilities or threats exist.
This information helps inform the selection and implementation of appropriate risk response strategies.
After implementing these strategies, organizations evaluate the residual risk to determine if it falls within acceptable levels based on their organization's risk appetite and strategic objectives.
If the residual risk is deemed too high, additional risk mitigation measures may be necessary to further reduce the risk to an acceptable level.
Business Impact Analysis (BIA) 💥
A systematic evaluation to identify and prioritize critical systems and functions, assess their dependencies and interdependencies, and establish recovery objectives
You can’t protect what you don’t know you have
Prioritizing where to focus control investments is crucial
Going back to the CIANA pentagon from Chapter 2, we’re very Availability focused, not as much Confidentiality and Integrity
So BIA’s might be done by your IT department or office of the CIO
CIOs are measured by Availability and performance of IT systems
CISOs more broadly consider confidentiality and integrity
It’s easy to protect a system from having its data stolen or being tampered with if you pull the plug out of the wall
But then we don’t have a business
And that’s why there’s some healthy tension between CIOs and CISOs and ideally they’d both report to the CEO
Other cool things about BIAs
The word Business Impact: it aligns our focus to enabling the business and not having technology for it’s own sake
It gets into dependencies and interdependancies
We know that technology is complicated
It can add a lot of value to the business to connect the dots with BIA work to discover that a system you didn’t think from your vantage point was very important was actually very important to someone else
the last thing is that it puts us in the “Not Urgent but Important” quadrant that is very often neglected in our fast paced lives.
URGENT | NOT URGENT | |
|---|---|---|
IMPORTANT | Crisis DETECT RESPOND RECOVER | GOVERN IDENTIFY —> BIAs PROTECT Planning, preparation Prevention Relationship building Personal growth |
NOT IMPORTANT | DMs | Binge watching |
Business Impact Assessment terminology:
Term | Definition | So what? |
|---|---|---|
Recovery Time Objective (RTO) | The targeted duration within which a business process or system must be restored after disruption to avoid significant impacts | How long will customers tolerate e-commerce being unavailable to buy your products, before they buy from your competitor? |
Recovery Point Objective (RPO) | Determines the maximum acceptable amount of data loss that are organization can tolerate | How many banking transactions can a bank afford to lose and have to re-create and reconcile? There is low tolerance for data loss here which makes a business case for expensive backup capabilities. |
Mean Time to Recover (MTTR) | The average time required to restore a failed system or process to full functionality after an incident | The AWS whitepaper below notes that while RPO and RTP measure objectives for one-time events, MTTR and MTBF measure mean values over a period of time |
Mean Time Between Failures (MTBF) | The average duration between two consecutive system or component failures | A longer MTBF indicates a more reliable system |
Term | Definition | So What? |
|---|---|---|
Single Point of Failure (SPOF) | Refers to a component or resource that, if it fails, would cause a complete failure of an entire system or process | Big availability risk Backup your password keeper or have on multiple endpoints Have multiple MFA options if you lose one In a business, is there a server that would result in a complete network outage? |
Mission Essential Functions (MEFs) | The key activities or processes that an organization must perform to maintain its core operations and fulfill its mission | A financial institution’s mission essential functions might include processing customer transactions, maintaining account balances, and ensuring regulatory compliance. |
Critical System | A system whose failure or disruption would significantly impact the organization’s ability to deliver essential services or fulfill its mission | If a system is deemed critical, it naturally should receive more resources and attention than one that is not considered critical. |
Critical System Examples
Domain Controllers: These servers manage all security-related aspects of user-domain interactions, including logging in, authentication, and directory services. If a domain controller goes down and no backup or redundancy is in place, users might be unable to access network resources, authenticate themselves, or perform tasks requiring security checks.
DNS Servers: These servers are responsible for resolving domain names into IP addresses. Without functioning DNS servers, network resources cannot be located, leading to failures in loading internet resources and accessing internal networks.
DHCP Servers: DHCP servers automatically assign IP addresses to devices on the network. If a DHCP server fails without a backup, new devices or those that renew their IP addresses may not be able to connect to the network.
Gateway/Router Servers: These servers manage traffic between different network segments and often connect internal networks to the internet. Their failure can isolate segments of a business network or disconnect the entire network from the internet.
Firewall Servers: They control the flow of traffic based on security rules to protect networks from unauthorised access and threats. A failure here can result in a complete halt in data flow, effectively cutting off network communication.
Email Servers: If an organization relies heavily on email communication internally and with external clients, the failure of an email server can severely disrupt business operations.
Database Servers: For businesses that rely on real-time data access for operations, the failure of a primary database server can halt many aspects of a business, especially if there is no failover or replication in place.
Financial Analysis 📊
Financial analysis assesses the costs, returns, and financial performance of cybersecurity measures. The following metrics help organizations make data-driven decisions regarding their cybersecurity investments.
Term | Definition | So What? |
|---|---|---|
Total Cost of Ownership (TCO) | The overall cost associated with owning, operating, and maintaining a particular asset or investment over its entire lifecycle | Considers both upfront costs and ongoing expenses, including hardware, software, personnel, training, and maintenance |
Return on Assets (ROA) | A financial ratio that measures the efficiency and profitability of an organization’s use of its assets to generate earnings Net Income / Average Total Assets | A higher return on assets indicates a more efficient use of assets to generate returns, while a lower return on assets suggests potential inefficiencies or inadequate cybersecurity measures. |
Return on Investment (ROI) | A financial metric that assesses an investment’s profitability and financial benefits relative to its cost Net profit or gain / Initial investment cost | A higher ROI indicates a more financially rewarding investment, while a lower ROI suggests a need for further evaluation or adjustment of the cybersecurity strategy. |
Conclusion and Touchpoints ✅
That wraps up risk management, which is going to be 20% of your A/CCRF exam.
It's about being that compass to help navigate and make decisions:
The risk management lifecycle guides organizations through a systematic approach to identify, assess, respond to, and mitigate risks.
It's about understanding the likelihood and impact of cyber risk so that we can introduce measures to buy it down to the appropriate place:
Understanding inherent and residual risks helps make informed decisions. Business impact analysis aids in prioritizing critical systems and establishing recovery metrics. Financial analysis evaluates the costs and returns of cybersecurity investments.
It's a life cycle. It's a process.
By applying these principles, organizations can enhance their cyber resilience and protect their digital systems and assets.
I'm excited for the next chapter! We're going to finally get into CSF, building on this foundation of risk. 🙌