Someone hands you a spreadsheet and says "implement NIST CSF." Now what?
I've been there. That experience stuck with me, and years later it's why Dr. Gerald Auger and I built something to bridge the gap between NIST's excellent guidance and actually doing the work. Then earlier this month, NIST featured it on their official resources page!
That means when organizations go looking for help implementing the framework, they'll find our free, open-source tool right alongside resources that helped me when I was starting out. Here's why we built it and how you can use it.
🎉 We made it onto NIST's official CSF 2.0 community resources page!
Some people talk about NIST CSF (believe me I LOVE talking about NIST CSF)
What if we took it further....
🥳 Steve McMichael, CPA, CCRP, CISSP, CISA and I built the Simply Cyber Academy CSF Profile Assessment Database to help organizations actually implement the NIST Cybersecurity Framework.
It's an open-source tool that lets you
✅ Track outcomes
✅ Assign ownership
✅ Document findings
✅ Score your security posture
✅ Track remediation progress.
YOWZERS!!! 🤩
Getting recognized by National Institute of Standards and Technology (NIST) on their official resources page alongside other community contributions is honestly incredible 💙
This means organizations looking to implement CSF 2.0 will now find our tool directly from NIST's own website 💪
Steve, what an absolute W!✨
To the Simply Cyber community...
This is for YOU 🥰
We built this to help practitioners do better work, and now NIST is amplifying it to help even more organizations reduce cyber risk.
The tool is free, open-source, and available on GitHub.
If you've got ideas to make it better, we're all ears.
🚨 Link to the tool
https://lnkd.in/ehgWgZFf
🚨 NIST's resources page
https://lnkd.in/eN3cdQUT
hashtag#freakingAwesome
Here's the backstory on why we built it and how you can use it. 👇
Table of Contents
Where This Started
When I pivoted from an inherited ISO27001-based GRC program to NIST CSF with a goal to improve cyber risk communication, someone handed me John Masserini's CSF Maturity Toolkit spreadsheet from NIST.gov, and it clicked.
Here was this effective way to roll up all the complexity that makes cybersecurity hard into just six functions. Govern. Identify. Protect. Detect. Respond. Recover. That's it. Six buckets that executives can actually understand, rolled up from 22 categories for managers and 106 sub-categories for practitioners.
I started thinking of CSF as both:
A better Generally Accepted Accounting Principles (GAAP) for cybersecurity
A better framework to demonstrate due diligence and due care - that you're running a comprehensive, defensible security program
The framework emphasizes resilience over just protection and covers both sides of a security incident:
Left of boom: Before something bad happens. Are your people, processes, and technology a soft target or a hard target? Are you governed well? Do you know what assets you have? Are they protected?
Right of boom: When a security incident inevitably happens (and it will). How quickly can you detect it? How effectively can you respond? How fast can you recover?
CSF gives you a structured way to assess all of it. And now NIST is pointing people directly to a tool that helps you do exactly that.
Back to Basics in Uncertain Times
Let me be direct about what this tool is and isn't.
It's NOT a Cadillac — It doesn't have continuous monitoring. It won't automatically harden your systems. If you're ready for that level of capability, check out my separate discussion with Jason Dion about the Continuous Hardening And Monitoring (CHAMP) program he set up:
It IS a powerful starting point. Especially for organizations that don't have deep technical bench strength or consultants who need a structured approach to deliver real value.
In times of uncertainty, there's massive value in getting back to basics, focusing on fundamentals. As Gerry puts it:
"Lather, rinse, repeat. Working through the cybersecurity framework outcomes, talking to people is how you become a baller GRC analyst!"
That's exactly what this tool enables — a systematic workflow for having meaningful conversations with control owners.
My Journey to Building This
I've been through the evolution many seasoned GRC practitioners have experienced:
Spreadsheets → The basics from nist.gov, and then evolving to custom spreadsheet workflows with macro scripts on a filer.

Ticketing Systems → Smoother workflow and more robust audit trail, but not designed for conducting assessments or extracting insights from the weeds to drive risk-reducing control remediation actions.
Enterprise Platforms (Hyperproof, CISO Assistant) → Powerful with better UI, but often more than you need when you're starting out or working with smaller organizations.
What I wanted was something that honored the fundamentals in reporting to senior management. Take the world-class guidance in NIST's excellent spreadsheet templates and elevate them to something dynamic enough to roll up, drill down, and actually drive conversations.
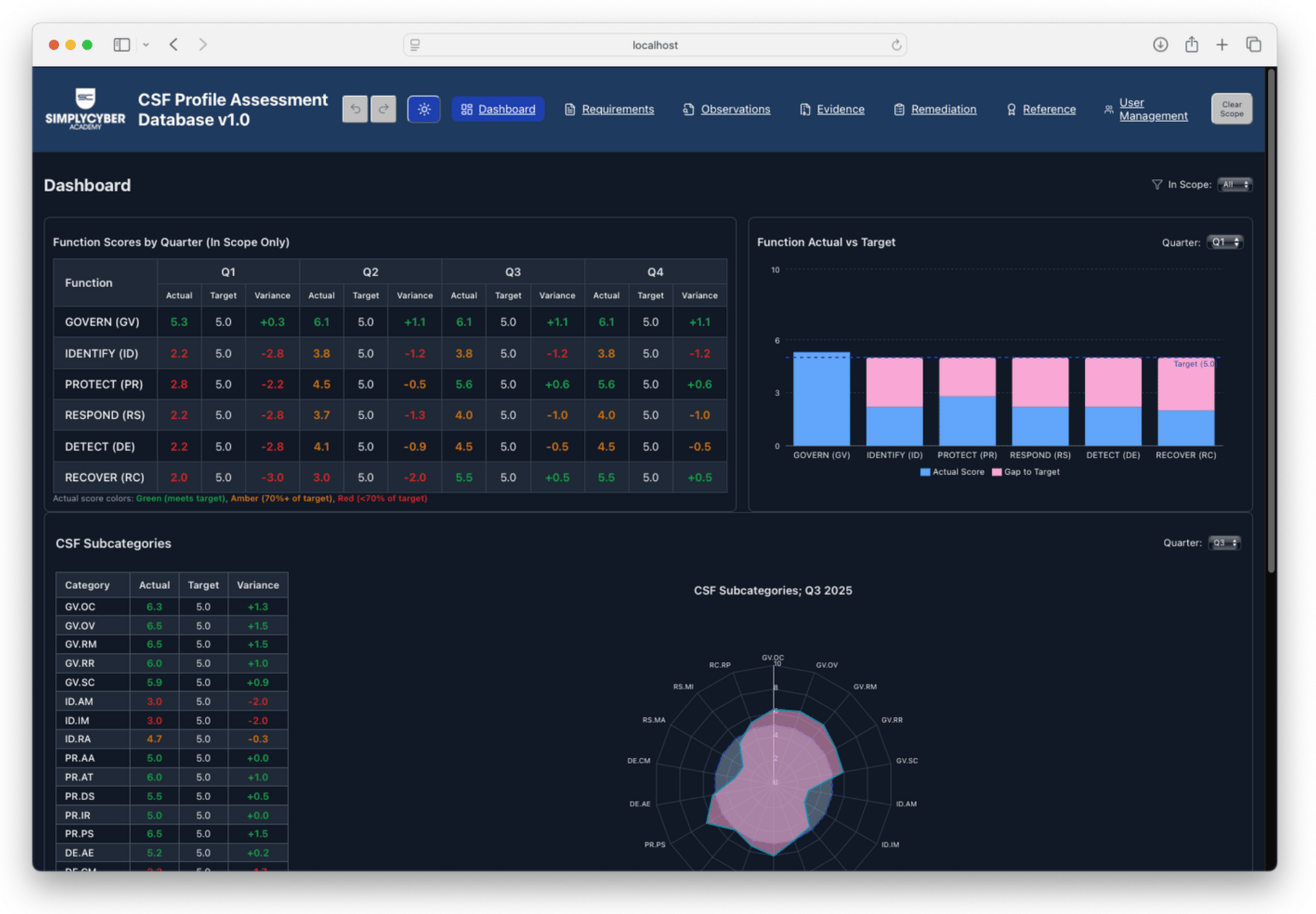
The result? A React-based application that:
Tracks all 106 CSF subcategories with 363 implementation examples
Scores current vs. desired security states on a 0-10 scale
Links artifacts directly to controls for defensible findings
Exports to CSV so you can analyze in Excel or feed into other tools
Creates a management trail that stands on its own
The Soft Stuff is the Hard Stuff: Benefits of This Approach Over Enterprise GRC Tools
The value this tool brings you is about enabling conversations that actually reduce risk.
Gerry made a sharp observation during our walkthrough: enterprise GRC tools are great for about the first month, then they fail. Why? Because culturally, the business isn't ready to take on all the responsibility and new workflows. You end up with shelfware.
The back-to-basics GRC Profile Assessment Database is built around what matters:
Talking to control owners - not just checking boxes
Documenting observations - creating that defensible management trail
Leading conversations - visual graphs that guide executives to the questions you want them to ask
Showing due diligence and due care - proof that you're doing the work
When an executive asks "are we secure?" That's a loaded question, and a better one would be "how resilient are we?" But with this tool, you can show them the six functions aggregated, let them drill into categories, and lead them to the gaps that need action plans. You're not just reporting status, you're driving outcomes.
What You Can Do With It
The workflow is straightforward:
Filter to in-scope CSF subcategories - Pick one implementation example per subcategory for a vanilla assessment
Work through each subcategory - Document your test procedures (inquiry + something else for trust-and-verify)
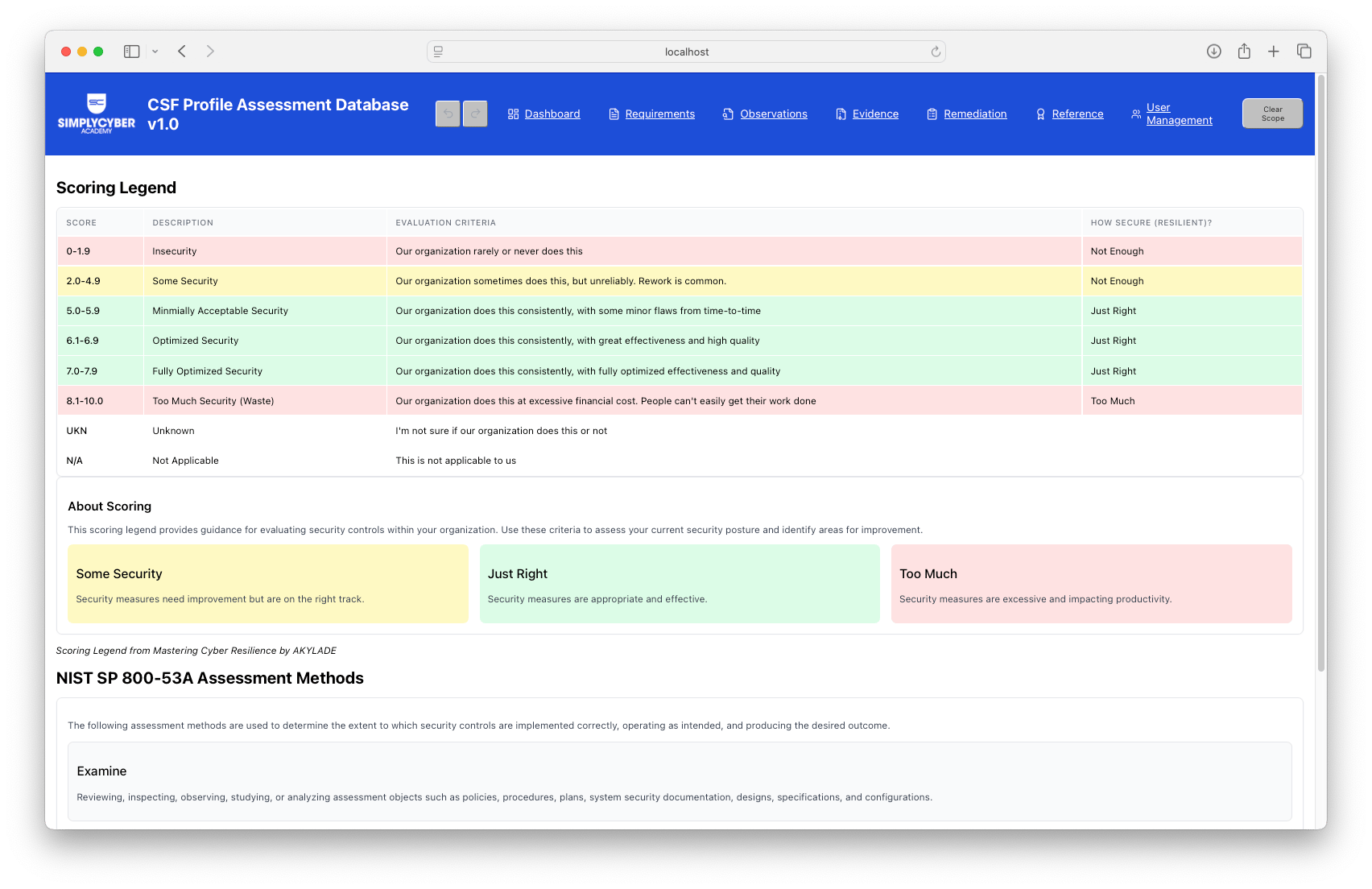
Score current and target states - Using a 0-10 scale based on the Mastering Cyber Resilience methodology: from "Insecurity" (0-1.9, rarely implemented) through "Minimally Acceptable" (5.0-5.9, consistent with minor flaws) to "Fully Optimized" (7.0-7.9). Anything above 8 is flagged as "Too Much Security" — excessive cost for diminishing returns.
Link your artifacts - Screenshots, tickets, policies — all traced to control IDs
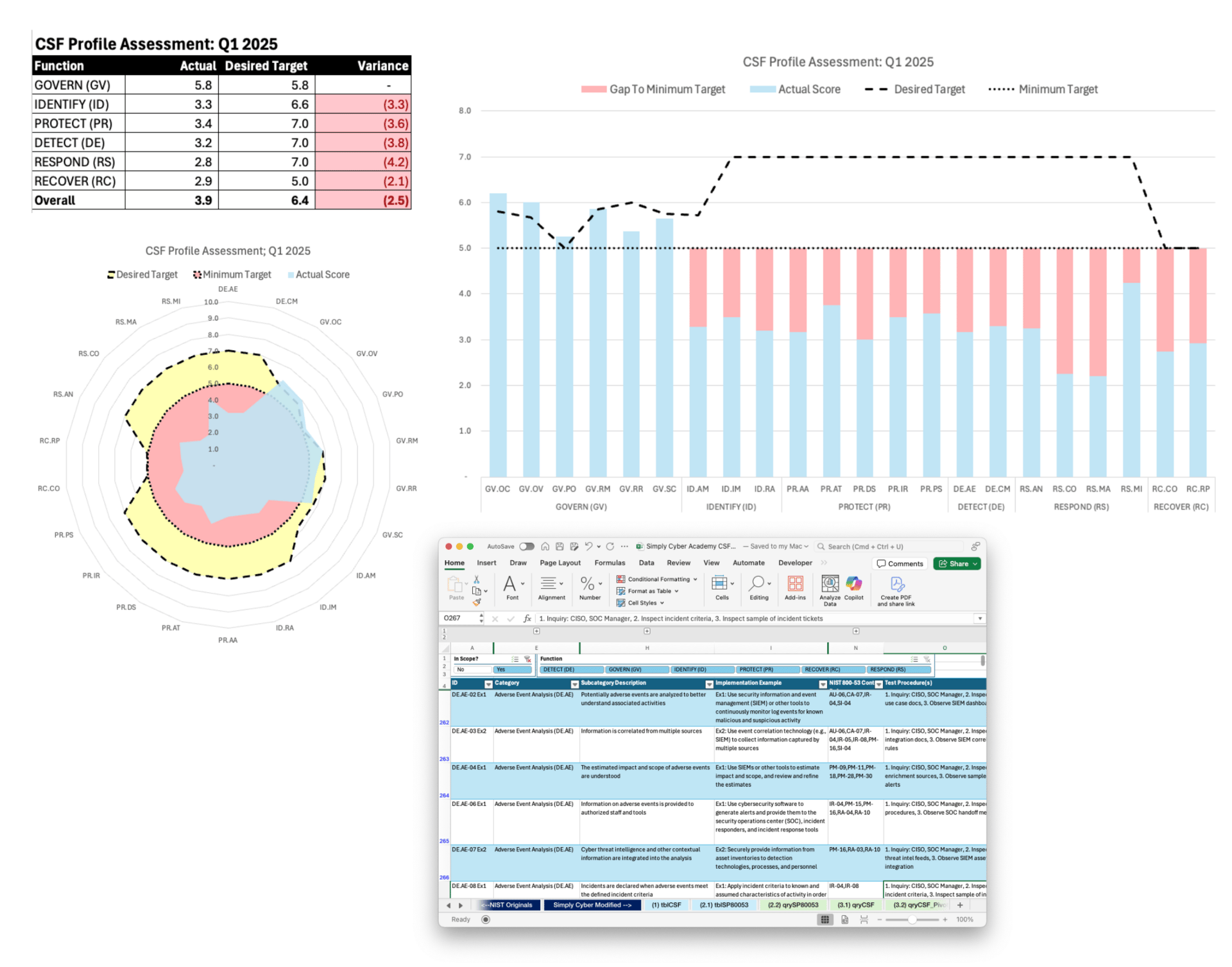
Export and visualize - Pull into Excel for those executive-ready bar charts and radar diagrams
Save for next year - Your first assessment is hunting; subsequent years are farming
The first pass takes effort. But when you come back next year, you're not starting from scratch. You're refining, updating, and building on documented work.
More a Stepping Stone Than a Destination
Another key theme from the discussion with Gerry is that this tool is part of a journey.
NIST guidance in Spreadsheets
⤷ Power Query
⤷ This tool
⤷ PowerBI/Tableau
⤷ Enterprise GRC platforms
Not everyone needs the end of that path. Many organizations, especially those working with consultants or building their first formal security program, need exactly what this provides: structured, repeatable, defensible assessments without the overhead.
It's about meeting organizations where they are. And for those ready to level up, this creates a natural bridge to more sophisticated tooling.
Your Feedback Welcome
This is an open-source community project. If you've got ideas to make it better, we're all ears.
Download it. Watch the installation and walkthrough videos. Apply it to your organization or the fictional Alma Security case study (included in the tool for practice). Submit issues on GitHub. Tell us what's working and what's not.
The Simply Cyber community built this together, and NIST is now amplifying it to help even more organizations reduce cyber risk.
Get Started
Free Tool:
NIST's Official Resources Page: CSF 2.0 Community Resources
Want to go deeper on CSF assessments and GRC fundamentals? Check out my Certified Cyber Resilience Fundamentals course at Simply Cyber Academy, or start with the free How to Break Into GRC | Mindset |Methods | Skills course if you're still exploring the field.

